 Catherine J. Frompovich
Catherine J. FrompovichThere have been a lot of theories about what could happen when Smart Meters (SMs) are tampered with and customers receive “false-reading, tampered-with” utility bills—water, gas, or electric—when hackers access the porous microwave networks that transmit in-the-house information that electric SMs constantly collect, then radio-transmit via microwaves back to utilities home offices.
That’s not some “pie-in-the-sky” theory; it’s of great concern to security experts!
According to Sally Ward-Foxton of Crosstalk (Oct. 2012)
But this increasing ‘digitalisation’ also adds a lot more opportunities for tampering with the meters in some way, resulting in security vulnerabilities. These vulnerabilities obviously need to be considered before introduction of the smart meters to make sure everyone is paying their way when it comes to electricity.Have tamper-proof-security-measures been instituted by utility companies?
Ward-Foxton discusses various scenarios regarding what can happen with computer programs, etc. to skew SM technology, plus safety and security issues for homeowners with SMs on their homes. However, that issue really needs to be taken seriously by everyone, especially utility companies who lobbied state legislatures to get SMs enacted in to law. Getting that legislation passed may be akin to “the dog that caught the bus”—don’t know how to handle the problem(s), or too big to handle. Fires, explosions, power surges are just part of the problems. Wait until hackers get into the system. We can only imagine the “fun” that will be, since we know what hackers can do via the Internet. However, SM microwave transmission is so ridiculously porous, that it just may be that everyone can try to see what he/she can accomplish, and any SM is fair game. Ward-Foxton states,
The data is also at risk when it leaves the meter – it’s usually transmitted wirelessly and there is a possibility that it could be intercepted. Obviously, it should never be transmitted unencrypted.The question consumers/customers ought to be asking of state regulators and legislators is this: Have you provided in law and via “Smart Meter Procurement and Installation Implementation Orders” generated by state Public Utility Commissions that every utility, which installs SMs, must use encrypted software to ensure transmitting accurate and tamper-proof SM meter reading information? If not, why not?
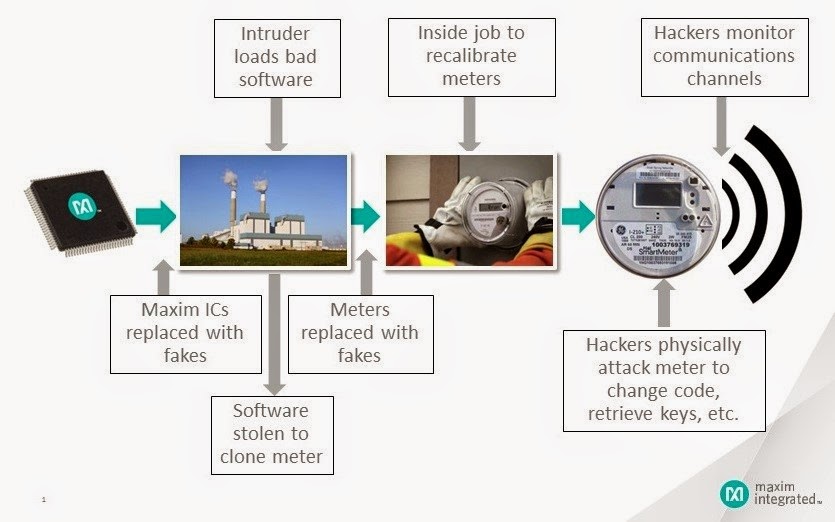
Chris Neil, Senior VP for Industrial and Medical Solutions Group at Maxim Integrated, summarized the problem on the slide below.
 |
| Source |
Recent trials focused on gauging the effectiveness of smart appliances and devices integrated with smart meters and dynamic pricing schemes have shown promising results, achieving significant decreases in peak demand and by extension reduced cost of energy.[Was that start-up, advertising talk—dynamic pricing schemes with promising results—reminiscent of utilities that wanted to introduce and pushed for nuclear power? The spin back then was that nuclear power would make electricity so cheap there would be no need for metering it [3]. Have customers forgotten that? Have you looked at your recent electric bills?]
However, most of this preliminary work has been based on simple decision-making algorithms to effectively control the on/off states of appliances as a function of pricing signals received. [Something that will drive customers to drink, I predict.] It also has been based on more granular schemes such as sub-metering at the device level, where customers are empowered to make more dynamic and well-informed decisions about their energy usage. The work is still in the early stages of development, largely due to a lack of cost-effective measurement devices for consumer appliances. [1][Will Smart Meters be in the same category as some computer software programs that constantly need updating because they have so many backdoors in them that were not found when sold to customers? Will Microsoft or Google be involved with your Smart Meters and computers too? Suppose you don’t like the way either does business? What are consumers to do?]
Furthermore, Ward-Foxton points out something SM meter customers are experiencing:
In California, a group of Stanford students saw their electric bill increase enormously after a smart meter was installed–even for a period when nobody was home and the breakers were turned off. The electric company said there was nothing wrong. After installing their own measuring device, the students found that the meter was overcharging them 2.5 times.SM customers around the country are complaining about horrendous increases in their electric bills since SMs were retrofitted on to their homes. Here are some examples:
Smart Meter Consumers Anger Grows Over Higher Utility BillsIf you have an SM, be forewarned!
https://sites.google.com/site/nocelltowerinourneighborhood/home/wireless-smart-meter-concerns/smart-meter-consumers-anger-grows-over-higher-utility-bills
FAQ: Billing Questions
http://stopsmartmeters.org/frequently-asked-questions/faq-billing-issues/
Smart Meter Complaints
http://emfsafetynetwork.org/smart-meters/complaints/
However, in the PECO utility service area of metropolitan Philadelphia, PA and suburbs, customers will be getting higher bills effective January 1, 2016, as PECO has filed for a $190Million rate increase on March 27, 2015.
If approved by the Pennsylvania Public Utility Commission, the increase would boost the total monthly bill for a residential customer using 700 kilowatt hours of electricity about $6.55 a month, or about 6 percent. The increase would go into effect Jan. 1.
Bills for all customers would go up about 4.4 percent. A typical small-business customer would pay about $27.72 more per month, and a typical large customer would pay $847.57 a month, Peco said. [4]With the ‘automatic’ SM increases and the new rate increase filing to take effect January 1, 2016, I wonder if PECO could be accused of price-gouging.
The other daunting concern that utility customers constantly are warned about is the power grid going down and what could happen. Will Smart Meters make the grid even more vulnerable than sun spots and the solar wind’s electromagnetic energy [2]? Any hacker—foreign or domestic—probably will be able to take down a utility, plus the grid itself, very easily once there’s a complete tie in to the U.S. Smart Grid, something those who don’t like America probably have on their drawing boards right now.
Frankly, all those ‘smart’ technologies seem rather dumb and make us more vulnerable, unless there’s a more sinister plot afoot like surveillance and control.
However, security breaches are addressed in the April 2015 report “Beware the Botnets” produced by BitSight Insights, which I downloaded.
The introductory paragraph states that
Major data breaches affecting some of world’s largest organizations have elevated cyber security to a top concern of executives and board directors. Beyond grabbing headlines, these data loss events can result in serious repercussions for businesses, including financial and reputational damage.They identify one import risk factor as botnets, i.e., “networks of computers that have been compromised or infected with malicious software and controlled as a group by an adversary without the owners’ knowledge. A botnet infection means that an attacker has obtained partial or complete administrative control of a system.”
In that report “BitSight examined the ratings of 6,273 companies with 1,000 or more employees, of which 199 (3.3%) had experienced at least one recent publicly disclosed breach” for the period March 2014 to March 2015. Finance, retail, healthcare, utilities, and education were the industries surveyed. According to BitSight, utilities were the second worst performer in their study! One botnet, Carufax, is a Trojan that is designed to steal personal data and information.
All this ‘smart’ technology does is create more problems to deal with; makes consumers spend more money either to own the ‘smart’ gadgets or comply with mandates/regulations like Smart Meter laws; and, ultimately, jeopardizes personal safety, and enables identity theft and other criminal activities via electronic devices.
About BitSight Technologies
BitSight Technologies [Cambridge, MA] is transforming how companies manage information security risk with objective, evidence-based security ratings. The company’s Security Rating Platform continuously analyzes vast amounts of external data on security behaviors in order to help organizations make timely risk management decisions.Do readers think that public utilities are safeguarding your personal information with Smart Meters?
References:
[1] http://electronicdesign.com/energy/you-can-t-have-smart-grid-without-smart-meters
[2] http://www.haystack.mit.edu/edu/pcr/Solar/files/PowerPoint%20Presentation%20-%20Introduction%20to%20the%20Sun%20and%20Space%20Weather.pdf
[3] http://media.cns-snc.ca/media/toocheap/toocheap.html
[4] http://articles.philly.com/2015-03-29/business/60582352_1_typical-small-business-customer-peco-distribution-charge
Catherine J Frompovich (website) is a retired natural nutritionist who earned advanced degrees in Nutrition and Holistic Health Sciences, Certification in Orthomolecular Theory and Practice plus Paralegal Studies. Her work has been published in national and airline magazines since the early 1980s. Catherine authored numerous books on health issues along with co-authoring papers and monographs with physicians, nurses, and holistic healthcare professionals. She has been a consumer healthcare researcher 35 years and counting.
Catherine’s latest book, published October 4, 2013, is Vaccination Voodoo, What YOU Don’t Know About Vaccines, available on Amazon.com.
Her 2012 book A Cancer Answer, Holistic BREAST Cancer Management, A Guide to Effective & Non-Toxic Treatments, is available on Amazon.com and as a Kindle eBook.
Two of Catherine’s more recent books on Amazon.com are Our Chemical Lives And The Hijacking Of Our DNA, A Probe Into What’s Probably Making Us Sick (2009) and Lord, How Can I Make It Through Grieving My Loss, An Inspirational Guide Through the Grieving Process (2008).
Subscribe to GLOBAL POLITICAL AWAKENING by Email
